Salaam, Namaste, Ola and Hello!
For those new to the blog welcome, and to those returning a big thanks! In part one of this series on ‘Azure Autopilot with Intune’ (https://iamitgeek.com/?p=123) I discussed what the Autopilot Service is, prerequisite requirements for this service and finally how to set it up.
In part two of the series I will now go through some of the user experience when logging onto a device that is added to the Autopilot Service as well as some features around the Intune profile you can setup to help manage the Windows 10 devices. As I have mentioned in previous blogs, I will be doing a separate series around ‘Intune Application deployment’ as its too big a topic to include here even though it has a big part to play with the Autopilot service.
Before any user’s login we really need to ensure that the device will be secure for them to use. Security of the device is controlled through the ‘Device Compliance’ section on the Intune portal and in here is where you can create policies for the different device types (Windows, Android, MAC and so on).

If you click on Policies > Create Policy, you can create your platform specific compliance settings your devices must meet to be allowed access to your corporate network. In this instance we need a Windows 10 compliance policy, however those who are familiar with the blog post I did on ‘Samsung Knox Enroll with Intune integration’ will see the settings you can configure for Windows 10 devices are very similar.

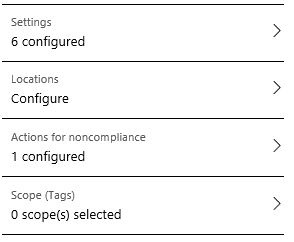
We have the Setting section which has:
- Device Health
- Device Properties
- Configuration Manager Compliance
- System Security
- Windows Defender APT
Device Health: Here you can configure if Bit locker encryption and Secure boot are required or not. Device Properties: You can specify the minimum and maximum OS level on your Windows devices. This isn’t really as significant as it is for mobile phone devices, however you may have an application that can only run on a specific build of Windows 10, so with this part of the policy you can ensure your devices meet that requirement. System Security: Here we configure the password requirement settings, including Password length, maximum minutes of inactivity, number of previous password and password type to name a few. Windows Defender APT settings are specific to Windows 10 and it lets you specify what minimum risk level the device needs to be at to be compliant. The final and in my opinion the most important setting is ‘Actions of non-compliance’ which defines what actions need to be taken for devices that do not meet the compliance policy requirements. The two actions around this are ‘Send email to end user’ or ‘Remotely lock the non compliant device’.
End User experience : After the compliance policy is set you are now in a position for the end users to login. The great thing about Autopilot service is that it allows the end user to have that out of box experience (OOBE) where they can remove the laptop from the original packaging and box as if they have just been out and purchased the laptop themselves, rather than have it handed over from IT with little marks on it from where IT have been using it to install the OS and configure the apps. The end user will need to choose the language, time/date, accept the license agreement and connect it to the Internet (via Wi-Fi). Once this is connected to the Internet the device makes that connection with the Autopilot service which already knows about this device as we imported it right at the start. It then loads a company specific login page that you can configure within Azure which includes your company name, logo and IT support contact details. The user then logs in with their corporate email address and Autopilot starts to install the compliance policy as well as any apps you have provisioned. The beauty of this is that there is no or very little management needed from IT, and rather than spend time on deploying devices, they can spend time working on the compliance and applications side.
That concludes my blog series on Autopilot with Intune folks, I hope you enjoyed this series and I would love to know what you thought so please feel free to leave a comment in the comments section. Until next time, ‘IamITGeek’ over and out!